Steam (macOS) – Local Privilege Escalation Vulnerability
In light of the recent news going around regarding Valve’s inaction and subsequent banning of a bug bounty hunter, we thought it was time to share our own terrible experience when it came to finding an LPE within Steam for macOS.
We’ve been doing a lot of macOS security research lately with an emphasis on insecure file operations including symlink attacks. Like most popular macOS software that we have tested, Steam was vulnerable to a basic symlink attack that would have allowed an unprivileged user to take over another user’s home directory. The end result is that any content within macOS can be compromised and root access obtained under certain circumstances.
The flaw was reported to Valve via their HackerOne bug bounty program and we were basically told that it did not meet the criteria for what they considered a credible security vulnerability. Eventually the flaw was silently patched with no acknowledgement or anything of nature and worst of all, older versions may still be vulnerable.
March 24:
We submit a report to HackerOne detailing a symlink attack that would allow an unprivileged user on macOS to take over another user’s home directory which could lead to a root level privilege escalation. The use case scenario would be Steam installed in a multi-user environment such as a school or a place of employment, etc.
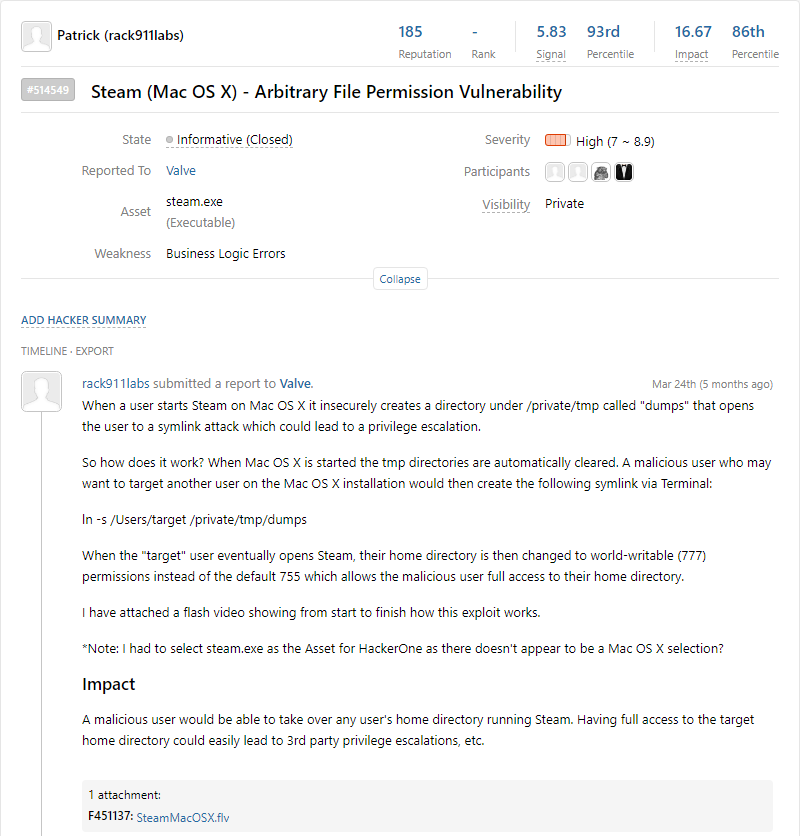
April 11:
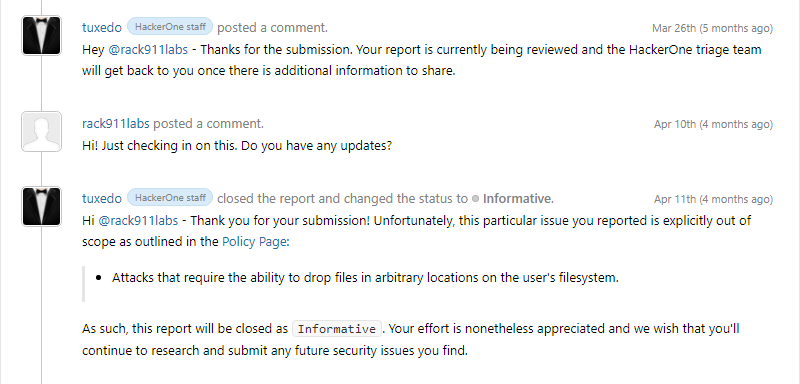
HackerOne informs us that the flaw does not qualify for any bug bounties because “Attacks that require the ability to drop files in arbitrary locations on the user’s filesystem.” making it ineligible. We have been doing a lot of security work on macOS software and this was the first time we came across a response that could only be described as being shrugged off, a non-issue if you will.
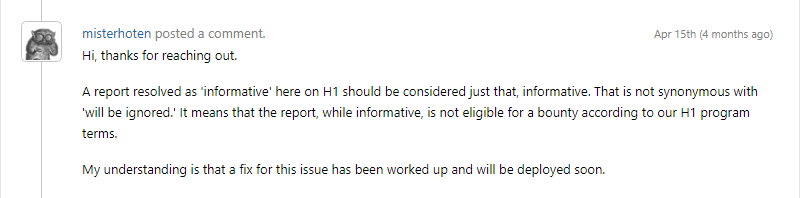
April 15:
Not happy with how the report was being handled on HackerOne, a direct email was sent to Valve’s security team where we told them our plan was to release the POC, but never did end up doing so, since they don’t seem to be taking our report seriously. We then received a reply via HackerOne instead of email:
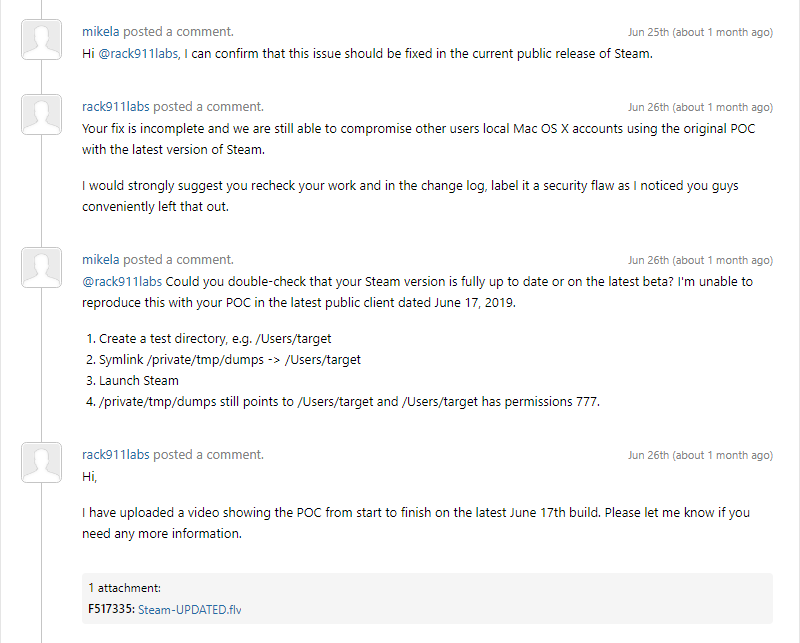
June 25/26:
Our initial submission with HackerOne was updated again asking Valve if they finally got around to fixing the security vulnerability. They replied back that Steam was indeed patched in the current public release.
Steam was opened on our macOS installation and updated from within the app. We then promptly re-tested our exploit and verified that the security vulnerability was still present! Version numbers were checked, the exploit was re-tested over and over to ensure that something on our end wasn’t the cause. Once we were confident that their fix was incomplete we informed them of such:
June 26th:
A couple hours later, Valve updates us and explains that we are using the old 32 bit binary of Steam which still has the security vulnerability because they only pushed out a new version which is now (apparently) 64 bit and has to be downloaded from the website:
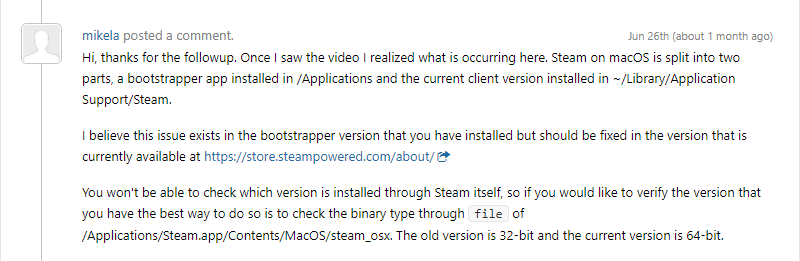
Steam was then uninstalled and reinstalled from their website. Upon installation, we were able to confirm that it is now indeed 64 bit and that the security vulnerability is no longer present. However, this presented an interesting situation because it would appear that updating Steam from within the app is not enough despite the end-user believing it is:
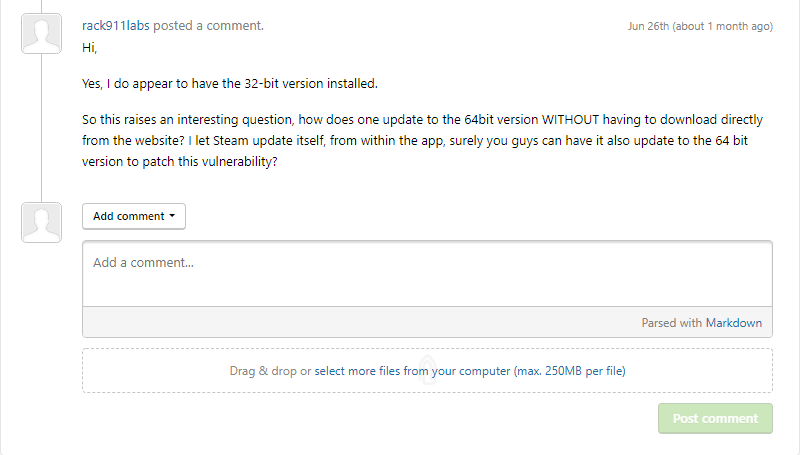
There have been no updates since June 26th and subsequent attempts to receive an update have gone unanswered.
We have worked with hundreds of companies over the last 6+ years and Valve has certainly earned a place near the top for lack of care both towards their end-users and security researchers who are only trying to help.
Want to talk about this? Send us an email [email protected] to discuss.