Ethical hacking for the real world!
Our penetration testing services are designed to identify not only real world threats, but also theoretical security vulnerabilities that could become a threat in a wide range of software.
Web Applications
Mobile Apps
Control Panels
Hosting Software
Ecommerce / Billing
WordPress Plugins
Operating Systems
Firewalls
IDS / SIEM / VPNs
Databases
ERP Systems
VOIP Platforms
Cloud Platforms
SaaS / PaaS / IaaS
VMWare / ESXI
KVM / Xen / Hyper-V
AWS / Azure / GCP
… and so much more!
Penetration Test Benefits
-
Peace of mind knowing that your software is protected from security vulnerabilities and free of backdoors from rogue developers.
-
Protect your brand and reputation from embarrassment should you ever be compromised.
-
Stay compliant with the various regulatory requirements of PCI-DSS, ISO 27001, HIPAA, SOX, etc.
-
Avoid costly lawsuits and Government fines should any sensitive data fall into the wrong hands.
-
Save time and money from not having to investigate potential security issues.
-
Have a third party expert opinion on where your security stands and address any shortcomings that have been discovered.
Auditing Process
A. When we perform a security audit, the very first thing we do is familiarize ourselves with your software. It’s important that we have a solid foundation of what your software is about and how everything is expected to work. We’ll interact with your software and treat it as if we were a real user, playing around with everything and making mental notes and observations as we go.
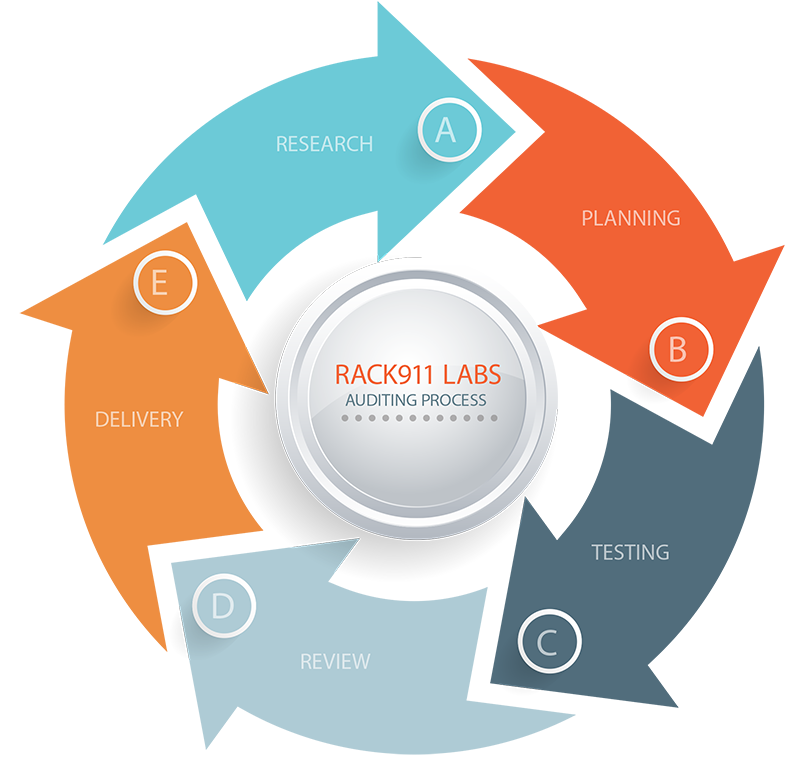
B. Once we are familiar with your software, we begin the process of mapping out every single feature into a detailed checklist. The checklist is basically a glorified flow chart and we follow it with precision to ensure that nothing is overlooked.
C. Using the checklist as our guide, we test every feature for a list of security vulnerabilities. As we work our way down the checklist, anything of concern is marked and we always indicate what types of security vulnerabilities were tested for each feature.
It’s important to note that all of our security testing is done by hand. We do reference OWASP testing practices and may run source code through automated vulnerability scanners, but only after our manual security test is performed.
D. After we have finished our testing, an audit report is prepared that contains the checklist, an itemized list of any security vulnerabilities found and detailed Proof of Concepts to allow your developer(s) the ability to recreate everything.
We also discuss general hardening advice, things that can be done to improve the overall security of your product. If any non-security bugs were found we always mention them as well. Our goal is to not only perform a security audit but also provide valuable QA feedback.
E. When we are completely done everything, the audit report will be sent to you in convenient PDF format. Our security analysts will be made available to discuss the audit report and ensure that you are satisfied and any followup questions are answered.
Why RACK911 Labs

Reputation
RACK911 Labs has been in business for many years with hundreds of security flaws to our name thanks to our cutting edge research.

Affordable
Our security services are some of the most affordable in the industry. We even have payment plans to work with most budgets!

Manual Testing
Every security test is performed manually using real world scenarios with the goal of not just thinking like a hacker, but outsmarting them.

Confidential
All interaction with us is held to the highest level of confidentiality. Whether you use our services or not, we will never discuss with a third party.

Clear Reports
All of our penetration tests include an easy to follow Audit Report to help you understand what flaws were found and how to resolve them.

Ongoing Support
We’re here to help! Whether you have questions or need ongoing security contracts to test every release, we have customized plans for that.